How to secure documents with Microsoft Azure Information Protection and Conditional Access
/Office 365 has long been associated with the strapline “work from anywhere, at any time and on any device”.
While this flexibility is great for end users, IT administrators often have security concerns with documents leaving the confines of the office network. But with mobile working on a variety of devices now the norm, are there better ways to protect your data?
Note that we did say “protect your data”, rather than “protect your network”, or “protect your infrastructure”.
The data is really the important thing here. While the security of your network remains important, the trend for data being held increasingly in SaaS services (such as Office 365) and that data being accessed on mobile devices from diverse locations means that simply securing the on-premises infrastructure is no longer sufficient.
So, what controls are there in the wider Microsoft 365 suite that can help?
Firstly, we see multi-factor authentication for all users in Office 365 as being the standard security stance. This does require additional licensing (in the form of Azure AD Premium) but is well worth the security controls and reporting you will get.
Although this blog post is about Azure Information Protection (AIP), I would like to briefly mention Conditional Access.
Conditional Access policies allow you to control not only whether a user can access a service and through which protocols, but also what devices they do it on and whether those devices are compliant with policies set in Intune.
Multi-factor authentication (MFA) can also be enforced with a Conditional Access policy.
Such policies are important as part of a layered approach to security.
Azure Information Protection – What’s in a name?
Azure Information Protection has evolved from a long history of established technologies from Microsoft that implement rights management protection. Because of this evolution, you might know this solution by one of its previous names.
Azure Rights Management Services (Azure RMS)
Azure Active Directory Rights Management
Windows Azure Active Directory Rights Management
Active Directory Rights Management Services (AD RMS)
Windows Rights Management Services (Windows RMS or WRMS)
Collectively, these technologies implement Information Rights Management (IRM) or Digital Rights Management (DRM). Most DRM solutions, however, typically protect against illegal distribution of digital content, which is very different from this enterprise information protection solution.
What can Azure Information Protection do for you?
Azure Information Protection is a cloud-based solution that helps an organization to classify, and optionally protect, its documents and emails by applying labels. Labels can be applied automatically by administrators who define rules and conditions, manually by users, or a combination where users are given recommendations.
A number of technologies are behind Azure Information Protection and the classification is achieved through the use of labels, which are now unified across Office 365.
Applying protection is achieved either by applying a label that has protection, or by a user choosing to protect certain data.
As an example, a user can choose to protect an email by clicking the “Do Not Forward” option.
The result is that, for the email recipients:
Copy and paste is disabled on protected content
Screenshots do not work
Screen sharing will result in black where the application window would be
Printing is disabled
The forward button does nothing
When replying, you cannot add new recipients to the replies
This kind of protection can be achieved because the encryption technology is baked into the Office applications. It is not, like a password-protected Zip file, a wrapper around the files. The actual content is protected. Office files such as Word, Excel, and PowerPoint can all be protected using AIP.
The experience for a recipient using the Outlook app on Windows is as follows. As screenshots are disabled, I used my phone to take the following screenshot.
How does it work?
It is important to understand that the Azure Information Protection feature does not require the data being protected to be processed by or stored in Azure or Office 365, although you can store it there if you want to, of course.
Azure RMS (Azure Rights Management Services), a component of Azure Information Protection, simply makes the data in a document unreadable to anyone other than authorized users and services:
The data is encrypted at the application level and includes a policy that defines the authorized use for that document.
When a protected document is used by a legitimate user or it is processed by an authorized service, the data in the document is decrypted and the rights that are defined in the policy are enforced.
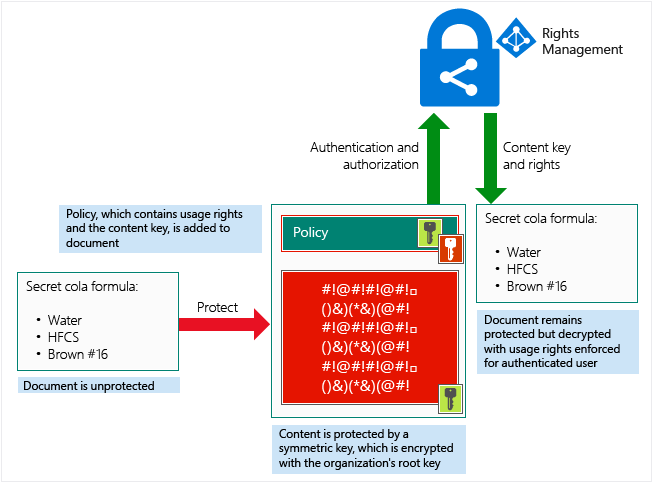
At a high level, you can see how this process works in the following picture. A document containing the secret formula is protected, and then successfully opened by an authorized user or service
The document is protected by a content key (the green key in this picture). It is unique for each document and is placed in the file header where it is protected by your Azure Information Protection tenant root key (the red key in this picture). Note, your tenant key can be generated and managed by Microsoft, or you can generate and manage your own tenant key.
Due to the way AIP works, when Azure RMS is encrypting and decrypting, authorizing, and enforcing restrictions, the document’s content is never sent to Azure.
The process works using technology that is now built in to the Microsoft 365 applications, and with a plugin (the Unified Labelling plugin) for Office 2016.
What are the requirements?
The requirements for individuals within your company who need to configure rights on a document are higher that the requirements for those consuming protected content.
For those protecting content
Microsoft provides an Azure Information Protection license which can be bought:
Standalone
As part of an Enterprise Mobility + Security (EMS) suite
As part of a Microsoft 365 Enterprise E3 license.
You will also need an Office application version that supports the Azure Information Protection features, and that means either:
Office 365 Enterprise E3; or
Office 365 Enterprise E5.
For those consuming content
If you are an external recipient, you would need a suitable email address:
Users of Hotmail, Yahoo or Gmail will be able to log in using those accounts and access content
If the recipient or their company uses Office 365, their email address will be supported without further action
If they use other email addresses (e.g. email provided by their company but not through Office 365), they will need to sign up for an account at https://aka.ms/rms-signup
Using a Windows PC
One of the following versions of Microsoft Office:
Office 2013 or later (all editions)
Office 365 ProPlus applications (as included in Office 365 E3, for example)
Office 365 Business applications (as included in Office 365 Business Premium, for example)
Excel Online (supported, but we expect most people will want to use our data in the full desktop applications)
Office 365 Home and Personal
The recipient or their IT department may have already installed the Azure Information Protection Client, but this is no longer essential for consuming content.
Using MacOS
You will need one of the following versions of Office:
Office 365 ProPlus: Office 2016
Office Standard 2016 for Mac
Using an Android device or an Apple iOS device
With Office Mobile or Outlook installed, users should be able to open protected documents without trouble.
Using web applications
Support for consumption and protection of content using web apps is rolling out across tenants and some features are still in development.
Revocation scenarios
When a user accesses protected content, they are granted a use license. It is possible to remove access to a protected file by revoking the use license for the file, so that users can no longer see the protected content even though they may have the encrypted file.
By default the use license is cached and valid for up to 30 days, as shown when attempting to revoke a document.
This means that revoking access is not immediate with the default settings, as demonstrated by the screenshot below.
In conclusion
We hope that has given you an introduction to some of the capabilities and features of the platform.
We haven’t covered some of the advanced features, including automatic classification and protection, but we feel that the options presented here are the ideal first uses for most customers.
Please talk to us if you’d like to know more about how we can help you being your journey with Azure Information Protection.