Introducing NSX-T 3.0: What’s New
/Today we see the release NSX-T 3.0 and it’s certainly been a busy time for VMware, especially their SDDC platform, which has seen several product updates with vSphere 7.0 and vSAN 7.0 also launching recently. With the release of vSphere 7.0 it’s not surprising to see NSX-T 3.0 have full stack support for modern apps running vSphere on Kubernetes.
It’s still hard to believe that there have been over 8 releases of NSX-T over the last few years and it appears there’s no let-up in development with a ton of new features in 3.0. Before I dive in a quick disclaimer, I was invited to a bloggers early access briefing and all the material shared in the post has been provided by VMware.
The slide below shows some of the key features available with NSX-T 3.0 and I’ll have a look at a few in more detail in this post.
NSX Federation
For me this was the probably the most obvious features missing that was available in NSX-V. Now true multi-site support is offered you can use NSX-T 3.0 for Disaster Recovery. This offers NSX networking and security services that can be consistent across different locations, and these can be on-prem, native cloud (AWS, Azure) and coming soon, VMware Cloud on AWS. All configuration is managed from a single UI to provide operational simplicity for both NSX-T Datacenter and NSX Cloud.
There are a few new components to briefly talk about. To provided consistent policy enforcement across all sites there is now an NSX Global Manager (GM) that pushes configurations to a Local Manger in each site. Network and security objects are shared between local managers, an example of this being group memberships.
One use case for this is for Disaster Recovery. In an active/standby configuration you would assign an active GM in Site-A and a standby GM in Site-B. You would have a T0 and T1 router configured and stretched between both sites with it being primary in Site-A, and secondary in Site-B. If Site-A were to fail then as part of the failover process you would first activate the GM in Site-B, then step 2 would be to make the T0/T1 routers primary in Site-B. This is done by either a couple of mouse clicks, or even better automated using a couple API calls. Following this you can begin the recovery of workloads using a product such as VMware Site Recovery Manger. This sounds really good and I can’t wait to try it out in a lab.
VRF Lite
Some welcome news for hosting providers or those that have multi-tenancy requirements. With NSX-T 3.0 you can isolate tenants using the same T0 router. The process is to create a VRF for each tenant as required up to a maximum of 100 per T0 gateway. NAT and Edge firewall services are supported on a per VRF basis. The effect of this reduces the number of edge nodes required in the environment so makes a better use of resources.
Converged VDS
As you can probably guess, with a new version of vSphere we get a new version of the vSphere Distributed Switch (vDS). When installing NSX-T 3.0 you can run it straight on top of the existing vDS without needing to change anything. Unfortunately, this is only the case for greenfield deployments, but the aim is to simplify installations and get new feature releases to customers faster.
NSX User Experience
I’m always keen to see improvements to the GUI and this release doesn’t disappoint. First, the policy and manager views have been split with a toggle to switch between views seamlessly.
Second are the getting started wizards. There are three to choose from to help you quickly prepare your environment for NSX-T.
Prepare clusters for VLAN Micro-segmentation
Prepare NSX Transport Nodes
Configure Remote Tunnel Endpoint.
I really like the VLAN Micro-segmentation option as I’ve seen a few customers start with this when deploying NSX into their environment.
Next is the Network Topology Visualisations (I’m a Brit so I spell it with an ‘s’). This feature provides a network diagram of the topology configured in your environment. A few other neat things with this are you have the option to both search and filter for object, and you can also export the topology to a PDF. Anyone who’s ever done any form of network troubleshooting knows the value of good, and more importantly, up to date network diagram.
Finally, a new alarm framework is available. There are many built in definitions but you can also build your own and manage them from dashboards. License enforcement will be in place with NSX-T 3.0 and these alarms can be managed from here.
NSX Distributed IDS/IPS
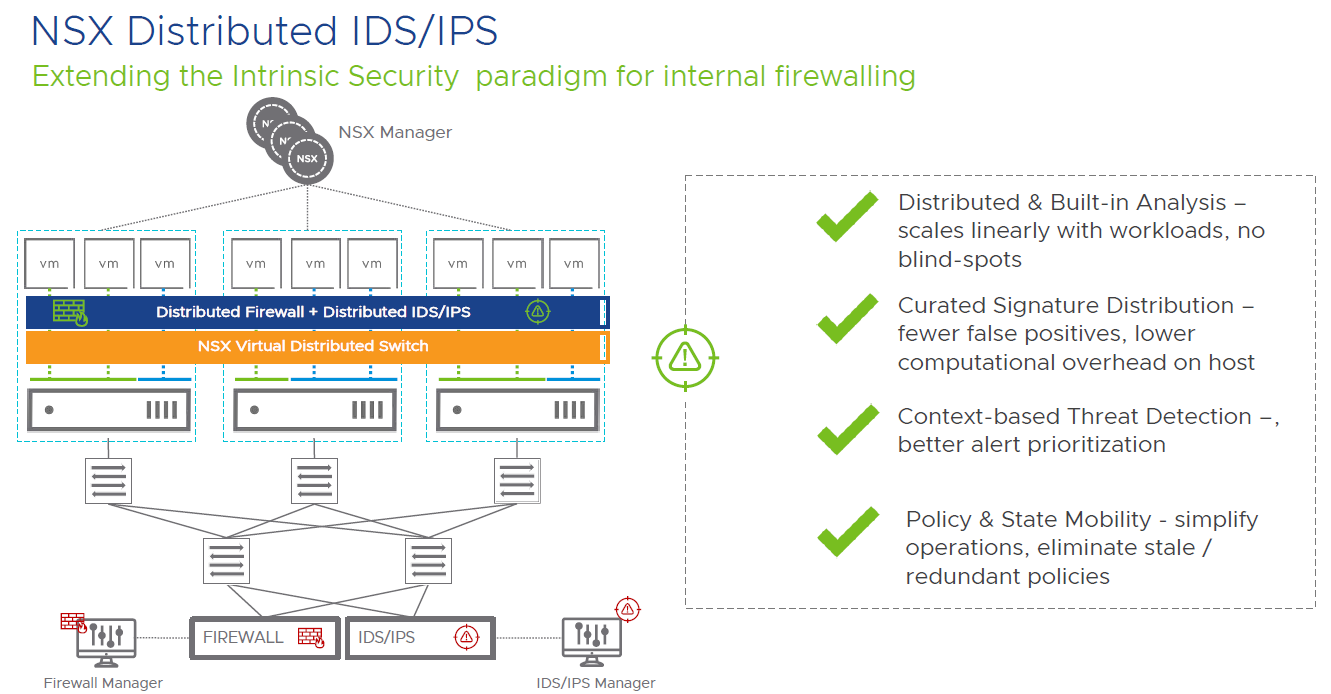
As this post is getting quite long, I’ll wrap up with a quick look at the Distributed IDS/IPS which is new to NSX-T 3.0. With traditional datacenter IDS/IPS usually involves a dedicated hardware appliance, or at least a hardware module in a firewall. The same issues are typically encountered with IDS/IPS that we had with traditional firewalls when trying to protect east-west traffic flows. Challenges such as hair pinning of traffic, lack of visibility and context mean that only certain traffic types are usually scanned. Distributed IDS/IPS in NSX-T 3.0 solves many of these challenges and works in a similar way to the distributed firewall that’s been around for many years. Once a host has been prepared for NSX-T the components for IDP/IPS are ready to use. As the service is distributed it can easily scale by adding hosts to the cluster. There are no longer blind spots in the environment as traffic can be inspected even if it never leaves the host.
Using Curated Signature Distribution ensures only the signatures are applied where they are relevant. An example of this would be signatures for Microsoft Windows vulnerabilities, there would be no point using these against Linux based workloads. This also helps to reduce the number of false positives and lowers the compute overhead. Context based threat detection using metadata collected with VM tools and guest introspection allows more insight into the workloads, like who is logged on and the application being used rather than just focusing on packets. Policy and state mobility mean the configuration moves with the VM as it moves to another host in the cluster, or even to another datacenter.
Summary
Hopefully this post has given you some insight to the new features that are coming with NSX-T 3.0 and help make your environments more secure than ever. I’ll finish with the summary slide listing all the new features and for further information I’ve included the link to the release notes.